Export Authorization Rules
-
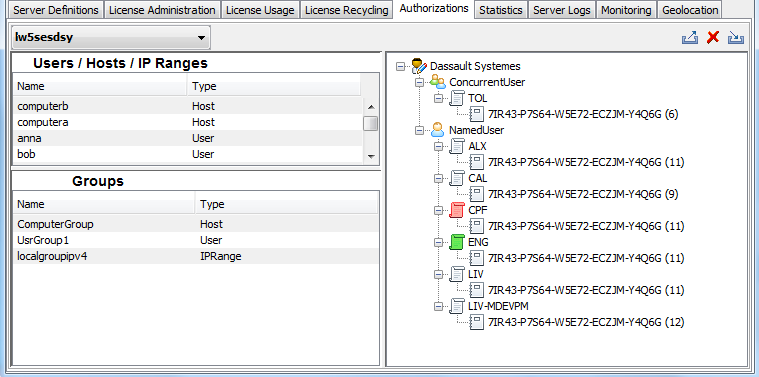
Select the Authorizations tab.
A toolbar is located in the top right corner of the tab:
The toolbar looks like this :

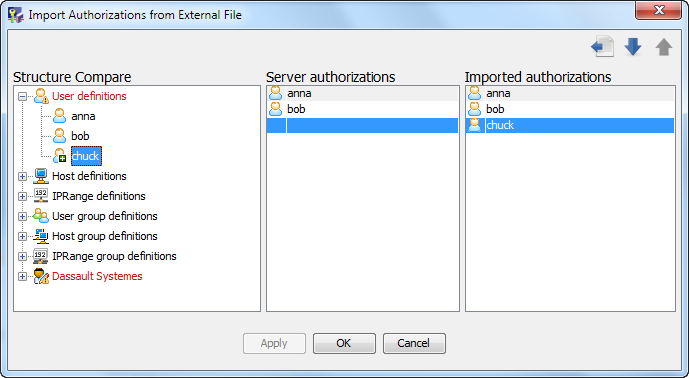
The first two buttons, from left to right (Export and Reset) are grayed out because at this stage you do not have any authorization data to export. However, the Import
 button is activated since you can at least import authorization data backed up in an existing XML file.
button is activated since you can at least import authorization data backed up in an existing XML file. -
Create some users, hosts, IP ranges and/or groups, and create some authorization rules linked to the data you created (as explained in Setting License Authorization Rules).
Once you have created all the data and rules, all the icons are activated like this:

-
Click the Export
 button and specify a file name in the dialog box displayed to save the file to XML format.
button and specify a file name in the dialog box displayed to save the file to XML format.
The XML file is structured as follows, for example:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <authorizations xsi:schemaLocation="http://www.3DS.com/DSLS DSLSAuthorizations.xsd" xmlns="http://www.3DS.com/DSLS" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <users> <user id="1">anna</user> <user id="2">bob</user> <user id="3">chuck</user> </users> <usergroups> <usergroup id="1"> <name>UsrGroup1</name> <user id="1"/> <!-- anna --> <user id="2"/> <!-- bob --> </usergroup> </usergroups> <hosts> <host id="1">computera</host> <host id="2">computerb</host> </hosts> <hostgroups> <hostgroup id="1"> <name>ComputerGroup</name> <host id="1"/> <!-- computera --> <host id="2"/> <!-- computerb --> </hostgroup> </hostgroups> <ipranges> <iprange id="1" cidr="10.232.0.0/16">local10232</iprange> <iprange id="2" range="192.168.0.1-192.168.0.255">local1921680</iprange> <iprange id="3" cidr="127.0.0.1/32">localcomputer</iprange> <iprange id="4" cidr="fd00::/10">localipv6</iprange> </ipranges> <iprangegroups> <iprangegroup id="1"> <name>localgroupipv4</name> <iprange id="1"/> <!-- local10232 --> <iprange id="2"/> <!-- local1921680 --> <iprange id="3"/> <!-- localcomputer --> </iprangegroup> </iprangegroups> <editor name="Dassault Systemes"> <model type="NamedUser"> <feature name="CPF"> <basicauthorizationlist ruletype="Deny"> <name>CPF</name> <user id="2"/> <!-- bob --> </basicauthorizationlist> </feature> <feature name="ENG"> <basicauthorizationlist ruletype="Allow"> <name>ENG</name> <host id="1"/> <!-- computera --> </basicauthorizationlist> </feature> <feature name="LIB"> <basicauthorizationlist ruletype="Reserve"> <name>LIB</name> <usergroup quantity="2" id="1"/> <!-- UsrGroup1 --> </basicauthorizationlist> </feature> <feature name="PRG"> <basicauthorizationlist ruletype="Limit"> <name>PRG</name> <hostgroup quantity="1" id="1"/> <!-- ComputerGroup --> </basicauthorizationlist> </feature> <feature name="IFW"> <offlinerestrictions> <name>IFW</name> <keyword>secret</keyword> <maxduration>21</maxduration> </offlinerestrictions> </feature> </model> </editor> </authorizations>Note: The<basicauthorizationlist>tag can appear directly under the<editor name>tag and not only under the<feature name>tag.For composite rules, the tag is
<compositeauthorizationlist>instead of<basicauthorizationlist>for standard rules. For example:<compositeauthorizationlist> <name>MDG,5LBGS-SIEJ7-TVIF0-UFAMA-EU0WX,NamedUser</name> <user rule="Deny" id="1"/> <!-- anna --> <usergroup rule="Reserve" quantity="5" id="1"/> <!-- ug1 --> <usergroup rule="Reserve" quantity="10" id="2"/> <!-- ug2 --> <host rule="Limit" quantity="5" id="1"/> <!-- host1 --> <host rule="Limit" quantity="25" id="2"/> <!-- host2 --> <iprange rule="limit" quantity="50" id="1"/> <!-- ipr1 --> </compositeauthorizationlist> ... <basicauthorizationlist ruletype="Allow"> <name>EDT,Token,5LBGS-SIEJ7-TVIF0-UFAMA-EU0WX</name> <user id="2"/> <!-- bob --> </basicauthorizationlist>
 button and click
button and click