EKL Profile Cards | ||
| ||
EKL Profile Card Mechanism
The Profile Card defines the function visibility as follows:
- Visible is usable and appears in the authoring UI.
- Hidden is usable but does not appear in the authoring UI.
- Forbidden cannot be used.
| Uses Local CPU | Reads from DB with Constant cost 0(1) | Reads from DB with Structure Dependent Cost O(n) | Modifies Target Objects |
|---|---|---|---|
| LocalCPU | ConstantRead | NonConstantRead | Modify |
Note:
In cases where no function or method has been declared, the visibility is defined as
Forbidden. When no argument or attribute category has been declared,
the category is specified as an internal error.
The EKL Profile Card is used by the Execution Control as follows: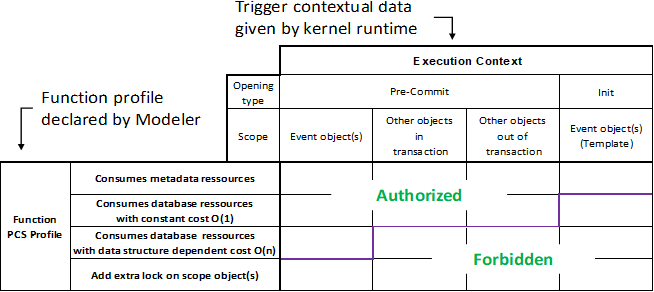
Profile Card Syntax
Function.Signature = FunctionName@Arg1Type@Arg2Type@..@ArgNType Function.Visibility = Visible | Hidden | Forbidden Function.Arg1 = LocalCPU | ConstantRead | NonConstantRead | Modify Function.Arg2 = LocalCPU | ConstantRead | NonConstantRead | Modify … Function.ArgN = LocalCPU | ConstantRead | NonConstantRead | Modify
Example 1
Function.Signature = Trace@Integer@String@Literal@... Function.Visibility = Visible Function.Arg1 = LocalCPU Function.Arg2 = LocalCPU Function.Arg3 = LocalCPU
Example 2
ComputedAttribute.Name = Feature.Children ComputedAttribute.Category = NonConstantRead