Restrict the Access to the Standalone ERAgent Port
It is better to restrict the IP addresses that can access the Standalone ERAgent
(/enovia-agent URI) to prevent other machines than the ER
connector host to get access to ENOVIA data.
Restrict the Access to the Standalone ERAgent PortIt is better to restrict the IP addresses that can access the Standalone ERAgent
( Configure a Reverse Proxy with HTTPSThe standalone agent does not offer an HTTPS connectivity by default. As login and passwords are sent to the agent in HTTP POST bodies, it is better to secure it
using an HTTPS reverse proxy. The reverse proxy with HTTPS is available on the ENOVIA server. You only need to add some entries to filter the ERAgent. To proxy
pass, reverse the The following diagram shows the basic security workflow. 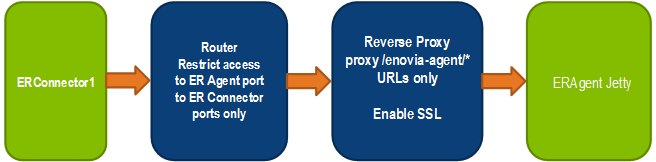 | |||||||||||