How Document Security Works | ||
| ||
If your network already has a security policy in place, you may want to reuse it for authentication in Exalead CloudView.
Note:
In Exalead CloudView, password, and login management is centralized and changes are automatically
propagated.
Configure a security source to authenticate users and authorize their
document access.
The document security workflow is described below.
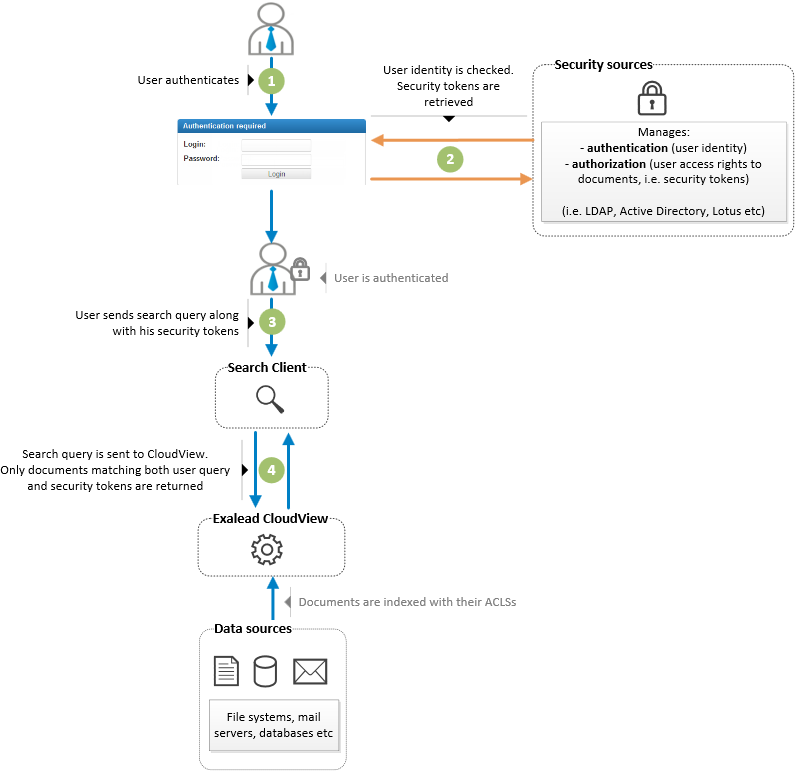
|
Step |
Description |
|---|---|
|
1 |
The user logs in to the Exalead CloudView search application. |
|
2 |
Exalead CloudView queries a security source for:
|
|
3 |
The user enters his search query. |
|
4 |
The user's query and security tokens are sent to the index. The index only fetches documents that match both the user's query and the user's security tokens. |