On the server side, the custom tokens of certificates
are delivered in two certificate files:
- OLCPCustomCertificateRequired.xml
- OLCPCustomCertificateSupplied.xml
On the server, you have two possibilities to deploy the custom
file:
General rules:
- custom tokens cannot overload inline tokens - an exception will
be raised if this happens. This can be easily prevented by avoiding DS reserved namespace
DS.internal to prefix custom token key. - If an external deployment is activated, then internal files
are overridden by the external files.
In the server, both
OLCPCustomCertificateRequired.xml and
OLCPCustomCertificateSupplied.xml files are delivered
in: .
$DeploymentRoot\enovia\WEB-INF\resources\logincertificates\sample
After WAR deployment to activate
these certificates, you must copy them to:
$DeploymentRoot\enovia\WEB-INF\resources
In the native app, both
PLM1.OLCPCertificateRequired.xml and
PLM1.OLCPCertificateSupplied.xml files are delivered in:
$OS\resources\logincertificates\sample
To activate these certificates you
must copy them to:
$OS\resources\logincertificates
The certificates are provider
dependent. For the native app, there will be two files for each
provider. 'PLM1' is the alias of the data provider, from the native app standpoint. Custom tokens cannot overload
in-lined tokens: an
exception will be raised if this happens.
This can be easily prevented by
avoiding DS reserved namespace DS.internal to prefix custom
token key.
Each certificate is composed of
a token. Each token is composed of
the following fields:
- Key:
identification name
- Rule: the
rule apply for token: Exit
- Comment:
additional information about content of token
The content of xml files are case
sensitive the available characters are: [a-z], [A-Z],
[0-9],[.]
Example of OLCPCertificateRequired.xml file:
<? xml version="1.0" encoding="UTF-8" ?>
<!-- OLCPCertificate Required certificate: Declaration of tokens required -->
< certificate >
<!--Token 'exist' rule-->
<!--Checks if the token is declared -->
< token key ="NewCustomDev1" rule ="exist">
<comment>New CAA development 1</comment>
</ token >
</ certificate >
Example of OLCPCertificateSupplied.xml file
<? xml version="1.0" encoding="UTF-8" ?>
<!-- OLCPCertificate Supplied certificate: Declaration of tokens supplied -->
< certificate >
<!--Token 'exist' rule-->
<!-The rule attribute is optional here-->
< token key ="NewCustomDev1" >
<comment>New CAA development 1</comment>
</ token >
</certificate>
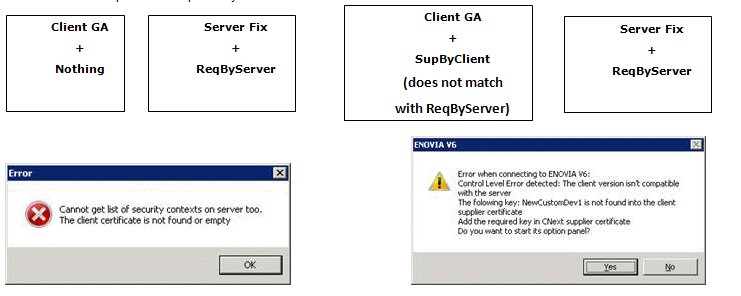
Case 1 : Client requires a compatibility check.
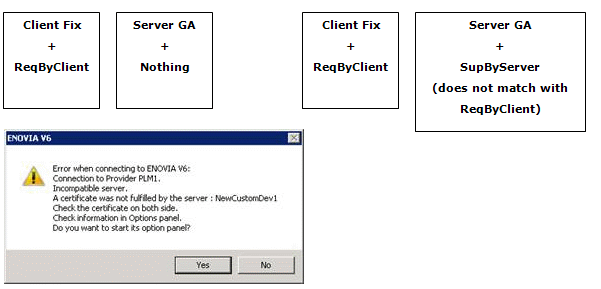
Case 2 : Server requires a compatibility check.