About FCS Network Security Views | |||||
|
| ||||
Client External View
The FcsClient library does not interact directly with the user. Therefore, the user application, which uses FcsClient, is responsible for gathering the appropriate credentials from the user.
Server External View
For server-to-server interactions, authentication is the only network security method that is supported. SSO is not supported. At an MCS/FCS server, user interaction is absent and credentials must be provided programmatically. System administrators can either use the out-of-the-box authentication management or implement their own custom authentication management by providing the java.net.authenticator class.
Client Internal View
The client internal view comprises SSO or authentication.
- SSO: Applications that use FcsClient for file operations are responsible for providing the cookie string containing a valid SSO cookie to FcsClient. If an SSO sign-on request is encountered (for example, 302 has temporarily moved or a cookie has already expired), FcsClient would throw an
FcsHttpResponseException(see sample code below). The application should catch this exception, usegetResponseCode()to verify the response code, and then usegetRedirection()to obtain the URL of the SSO sign-on page. Then, the application should redirect the user to the SSO sign-on page. Once the sign-on is (re)established, the application could invoke FcsClient again with the newly acquired SSO cookie string.public class FcsHTTPResponse extends Exception { public int getResponseCode() public String getResponseMessage() public String getErrorMessage() public String getRedirection() public String getMessage() } - Authentication: Applications that use FcsClient should provide a default implementation for the authenticator class. Applications that run inside a browser should automatically get the default authenticator from the browser, which can prompt the user through a dialog to enter their username and password. The application should call
Authenticator.setDefault(<authenticator_implementation>)to set your implementation to the default authenticator. ThegetPasswordCredential()method of the authenticator class can be called whenever an authentication takes place and the credential is needed. This method should prompt the user to enter their credential, and return it accordingly. For details, seejava.net.Authenticatorandjava.net.PasswordAuthentication. - The FCS Tools
FcsSubmit and FcsRescue can be used to debug the authentication functionality.
- To use the default authenticator with a credentials file, use the
-authenticateoption as follows:FcsSubmit ... -authenticate <credentialsfile>
- To use a custom authenticator, use the
-authenticatoroption as follows:FcsSubmit ... -authenticator <myauthenticator>
- To use the default authenticator with a credentials file, use the
Server Internal View
- SSO: Not supported in this view
- Authentication:
- Custom Authentication Management
- Out-of-the-Box (OOTB) Authentication Management
- Without Encryption: OOTB authentication management can be implemented without encryption by putting the credentials file in place and setting
MX_HTTP_DEFAULT_CLIENT_AUTHENTICATIONto true.0. At startup time, the credentials file is retrieved.
1. Upon receiving an authentication challenge, FCS first extracts the challenge information.
2. Then using that information, it obtains the appropriate credential.
3. Finally, it sends the credential out for authentication.
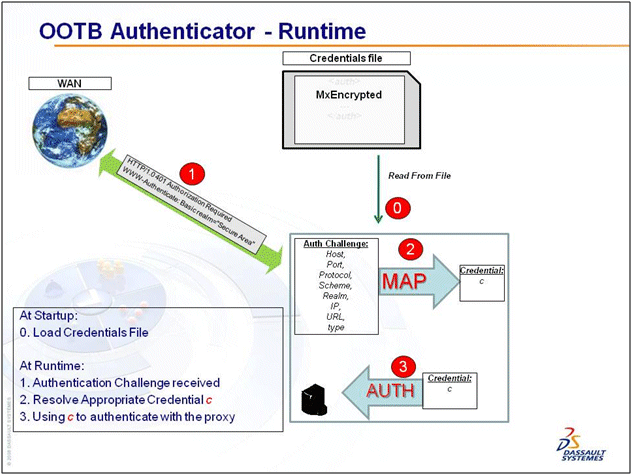
- With Encryption: OOTB authentication management can be implemented with encryption as follows:
-1. After running
MxEncryptCredentials.classwith the credentials files (andMX_HTTP_DEFAULT_CLIENT_AUTHENTICATIONandMX_ENCRYPT_NETWORK_CREDENTIALSboth set to true), the encrypted credentials file is generated.0. At startup time, the credentials file is retrieved and decrypted.
1. Upon receiving an authentication challenge, FCS first extracts the challenge information.
2. Then using that information, it obtains the appropriate credential.
3. Finally, it sends the credential out for authentication.
- Without Encryption: OOTB authentication management can be implemented without encryption by putting the credentials file in place and setting