-
Right-click the central panel, and select Sources > ENOVIA
SECURITY.
-
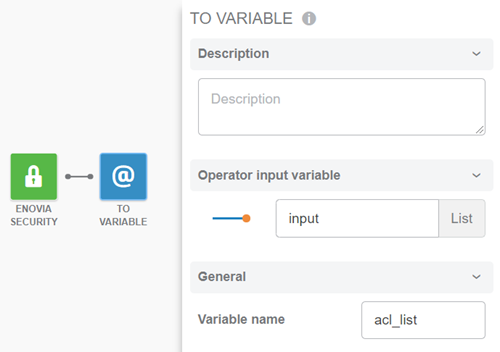
Drag the point of the first operator, and select Terminal > TO
VARIABLE.
-
In the right panel, go to the General section, and for
Variable name, enter
acl_list.
-
To filter your results, you can now define the following expression in your
SEARCH or FILTER operator.
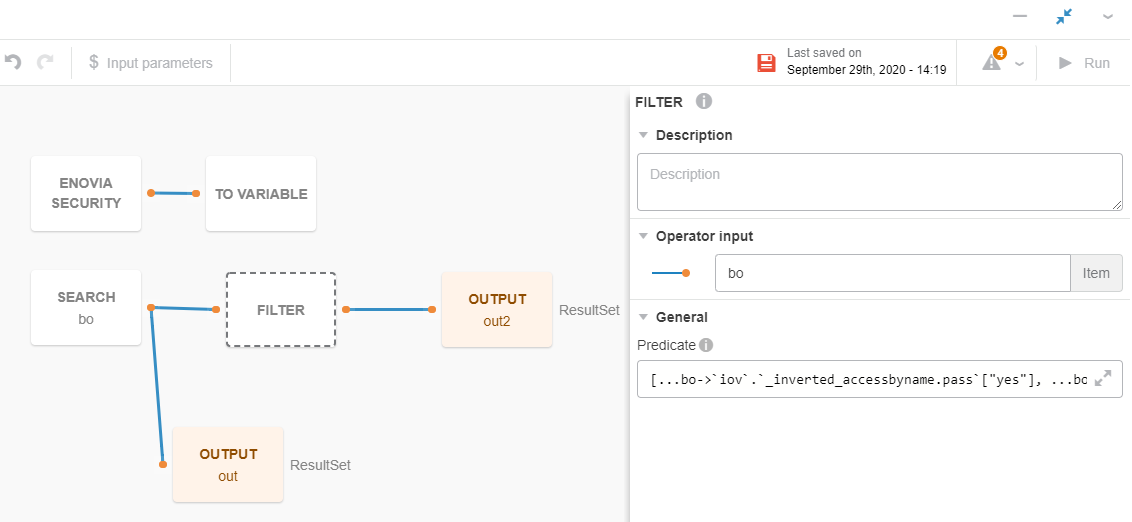
[...bo->`iov`.`_inverted_accessbyname.pass`["yes"],
...bo->`iov`.`_inverted_accessbyname.pass`["maybeYes"],
...bo->`dov`.`_inverted_accessbyname.pass`["yes"],
...bo->`dov`.`_inverted_accessbyname.pass`["maybeYes"]].anyMatch(v => v IN @acl_list)
Where:
-
acl_list - is the variable name that contains the ENOVIA user rights.
-
bo - is the variable that contains the input stream.
Example of SEARCH operator configuration:

Example of FILTER operator configuration:
|