Sample scenario
This section will use the Files system and SolidWorks PDM connector scenario as an example. Don’t worry if you don’t use SolidWorks PDM: the process is the same for other PLM data sources such as SmarTeam or Enovia.
Context:
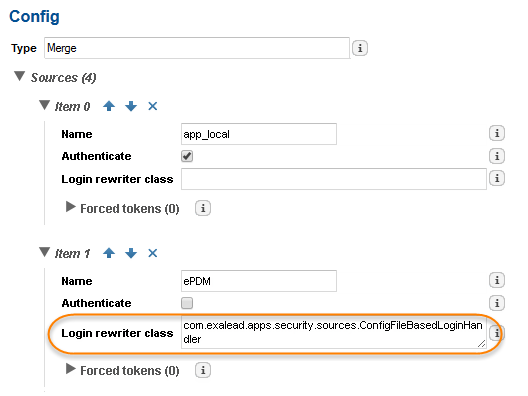
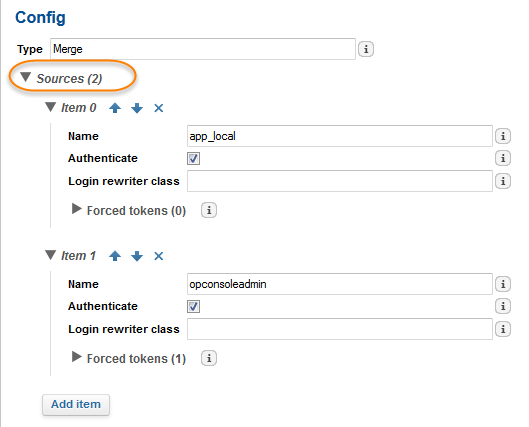
In our sample scenario, your documents come from two different types of connectors, each with its own security rules:
-
the first one is based on your SolidWorks PDM instance
-
the second one is based on your filesystem security (LocalWindowsSecurity or ActiveDirectory).